Delay, Loss, Throughput in Networks
Delay in networks
Packets queue in router buffers
- When packet arrival rate to link (temporarily) > output link capacity -> packets queue, wait for turn
d = $d_{proc}$ + $d_{queue}$ + $d_{trans}$ + $d_{prop}$ -> 한 라우터를 거쳐갈 때마다
- $d_{proc}$: processing delay, determine output link by forwarding table lookup, 무시해도 되는 정도
- $d_{queue}$: queueing delay, tme waiting at output link for transmission, 계산 어렵
- $d_{trans}$: transmission delay, $L/R$ where L = packet lengths(bits), R = link bandwidth (bps)
- $d_{prop}$: propagation delay, $d/s$ where d = length of physical link, s = propagation speed
- time for 1 bit to travel 1 link
E2E (end-to-end) Delay for 1 pkt = $(d_{trans} + d_{prop}) * # of hops in E2E path$
E2E Delay for whole msg = $E2E Delay for 1 pkt + d_{trans} * (n-1)
$D_{trans} < D_{prop}$
- 1st bit doesn't arrive at next router when all bit of pkt is transmitted
- ex. Satellite link network
$D_{trans} > D_{prop}$
- 1st bit arrive at next router befoe all bit of pkt is transmitted
- ex. 우리가 쓰는 대부분의 ground network
Traffic Intensity (TI) at Output Queue
- TI = $La / R$ where R = link bandwidth (bps), L = pkt length (bits), a = average pkt arrival rate
- TI < 1, 1에 가까워질 수록 queueing delay 커짐
- In reality, burst traffic intermittently arrives at queue -> Variations in pkt arrival rate
"Real" Internet delays and routes
- Traceroute program (= tracert): 인터넷을 통해 거친 경로를 표시하고 그 구간의 정보를 기록하고 인터넷 프로토콜 네트워크를 통해 패킷의 전송 지연을 측정하기 위한 컴퓨터 네트워크 진단 유틸리티
Packet Loss
- In Packet Switching, there is no resource reservation and they have finite buffer -> Packet loss at output buffer can occur.
- Packet arriving to full queue is lost (dropped)
Throughput
- E2E path (multiple link)로 측정: 단위 시간 당 end host에서 end host로 전송되는 bit 수
- rate (bits/time unit) at which bits transferred btw sender / receiver
- (BW or Data rate or Transmission rate R) / over 1 link
- Bottleneck link: link on e2e path that constrains end-end throughput
- $min(R_i) where i in the e2e path$
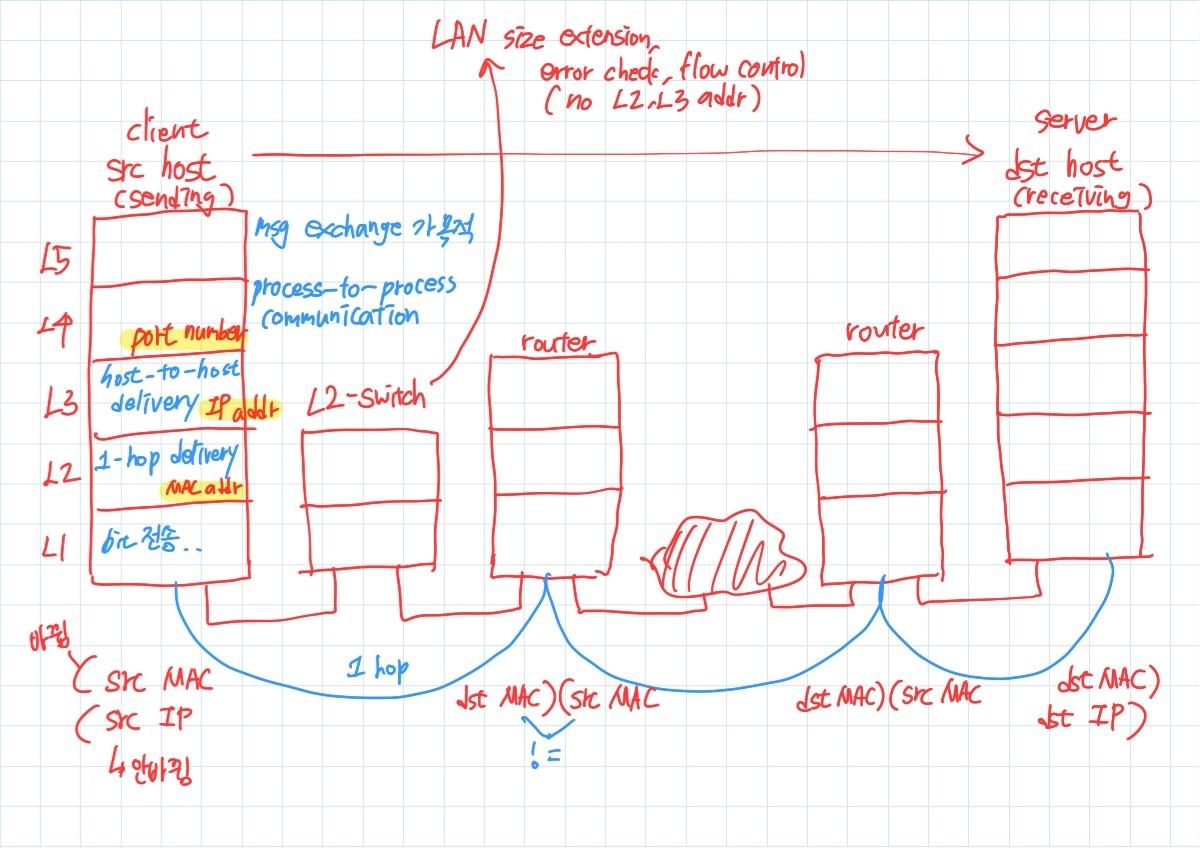
Protocal Layers
Protocol Layers
Why Layering?
- dealing with complex systems
- modularization eases maintenance, updating of system
- change of implementation of layer's service transparent to rest of system
- Cons
- one layer may duplicate lower-layer functionality
- cross-layer protocol -> violate layering
5-Layer Internet Protocol Stach
- Application (L5): supporting network applications
- FTP, SMTP, HTTP
- msg (Protocl Data Unit a.k.a. PDU)
- Transport (L4): process data transer
- TCP, UDP
- segment (UDP는 segment X)
- Network (L3): Routing of datagrams from source to destination
- IP , routing protocols(BGP, OSPF, RIP)
- datagram or packet
- Link (L2): Data transfer btw neighboring network elements
- Ethernet, 802.11 (Wifi), PPP
- frame
- Physical (L1): bits on the wire
Network Application을 P2P(peer-to-peer) 구조로 설계할 때 고려해야 할 문제
- P2P 서버에 해당하는 peer가 사설 IP 주소 (private IP address)를 가지는 경우가 있으므로, 정상적인 서비스 동작을 위해서는 라우터에 추가 기능이 필요하다.
- P2P의 서버(peer)는 주로 개인 호스트이므로 이 호스트가 위치한 access network가 residential network인 경우 해당 ISP의 uplink가 서비스 품질(throughput)의 bottleneck이 될 수 있다.
- Peer들이 인터넷 곳곳에 분산(distributed)되어 있고 하나의 관리자가 운영하는 것이 아니므로 보안을 강화하기 어렵다.
Networks Security
Put malware into hosts via Internet
- malware can get in host from:
- virus: 기생해서 실행, 사용자 개입 필요, 컴퓨터 내 공격
- worm: write once read many, 독자적으로 실행, 사용자 개입 필요 X, 네트워크(server, link) 공격
- zero day attack: 소프트웨어가 출시된 후 patch가 나오기 전에 취약점을 공격하는 malware
Denial of Service (Dos)
- attackers make resources unavailable to legitimate traffic by overwhelming resource with bogus traffic
- infected host can be enrolled in botnet, used for DDoS attacks
Sniffing
- Packet Sniffing
- broadcast media
- promiscuous network interface reads/records all packets passing by
- IP spoofing: send packet with false source address
- man-in-the-middle-attack
- Solution: end-point authentication
Internet History
1961-1972
Early packet-switching principles
- queueing theory -> packet switching -> first ARPAnet
- NCP(Network Control Protocol first host-host protocol
- first e-mail program : 최초의 인터넷 서비스
1972-1980
Internetworking, new and proprietary nets
- ALOHAnet, Ethernet
- Internetworking Principles
- 하나의 관리자에 의해 제어되지 않는다 - decentralized control
- 라우터들이 호스트에 전송한 패킷들에 관한 정보를 유지하지 않는다 - stateless routers
- end-host들이 요구하는 서비스 품질을 보장하지 않는다 - best effort service model -> good for heterogeneous link
- 갹 ISP들의 자치권(최소한의 변경으로 ISP 망 연결)을 보장한다. - minimalism, autonomy: no internal changes inquired to interconnect networks
1980-1990
New protocols, a proliferation of networks
- TCP/IP, various application protocols
- smtp e-mail protocol, DNS, ftp, TCP congestion control, NSFnet
- flow control v.s. congestion control
- 공통점: 버퍼의 overflow을 막음
- 차이점: flow control은 receiver의 버퍼를, congestion control은 router의 버퍼를 제어
1990 - 2000's
Commercialization, the Web, new Apps
- hypertext Web, HTML, HTTP
- P2P file sharing, network security
2005 - present
- smartphones and tablets
- ubiquitous deployment of wireless and broadband access
- social networks, content provider networks, cloud service
'CS > 컴퓨터네트워크' 카테고리의 다른 글
| [Ch3] UDP, TCP (1) | 2023.11.21 |
|---|---|
| [Ch2 & Ch3] CDN, UDP & TCP, Mux & Demux (1) | 2023.11.14 |
| [Ch2 Application Layer] Electronic Mail, DNS, P2P applications (1) | 2023.11.02 |
| [Ch2 Application Layer] Principles of Network Applications, Web and HTTP (0) | 2023.10.30 |
| Week 1: Network Edge, Network Core (0) | 2023.10.17 |
